Compliance as a Service (CaaS) helps businesses manage data privacy and security without the complexity of DIY compliance. Learn how it works and why it matters.
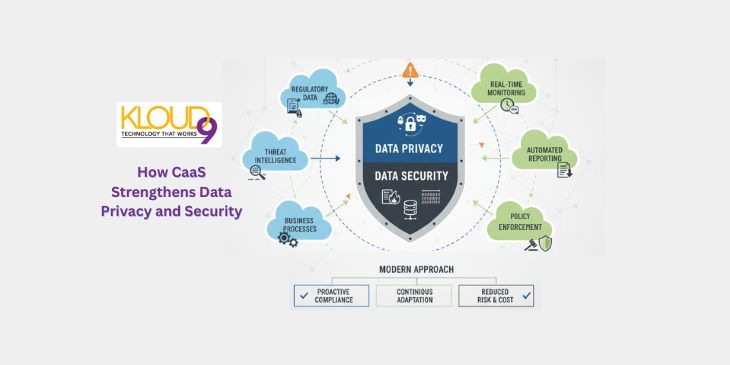
CaaS for Data Privacy and Security: A Modern Approach
VoIP Security Essentials: How to Keep Your Business Calls Safe
2025 Trends in Managed IT Services: Automation, AI, and Beyond
The IT Checklist Every Business Owner Should Follow (But Most Ignore)
What Are The Security Risks Associated With Cloud Computing, And How Can They Be Mitigated?
How Can Cybersecurity Solutions Mitigate Risks and Safeguard Your Organization?

In this digitally-driven landscape, the increasing frequency and sophistication of cyber threats pose significant challenges to organizations worldwide. From data breaches to ransomware attacks, the consequences of cyber attacks can be devastating, impacting financial stability, reputation, and customer trust.
Strengthening Your Digital Defenses: A Comprehensive Guide to Cybersecurity
Ramp up your defenses with proactive cybersecurity

Cyberthreats are becoming more sophisticated every day, and if your business isn’t taking steps to protect itself from these threats, it faces a high risk of falling victim. This can cause you to lose valuable data or even go out of business. In this blog post, we will discuss what proactive cybersecurity is and how it can help protect your business against ever-evolving cyberthreats.