The year 2025 might have started like every other year, but it is here with its perks for the near future, especially in business. Automation, cloud computing, artificial intelligence, and more are revolutionizing managed IT services.
2025 Trends in Managed IT Services: Automation, AI, and Beyond
What is single sign-on and why should you be using it

If you use multiple applications and accounts for work, you know how frustrating it can be to have to enter different usernames and passwords for each one. That's where single sign-on comes in.
What is single sign on?
Single sign-on or SSO is an authentication method that lets users access several applications and websites with a single set of login credentials.
7 Ways to keep your email account safe
Defending against watering hole attacks

More and more cybercriminals are launching watering hole attacks to gain access to company networks. But what exactly is a watering hole attack, and how can you protect yourself from it? Read on to learn how.
How watering hole attacks work
The term “watering hole” colloquially refers to a social gathering place where a particular group of people often go to.
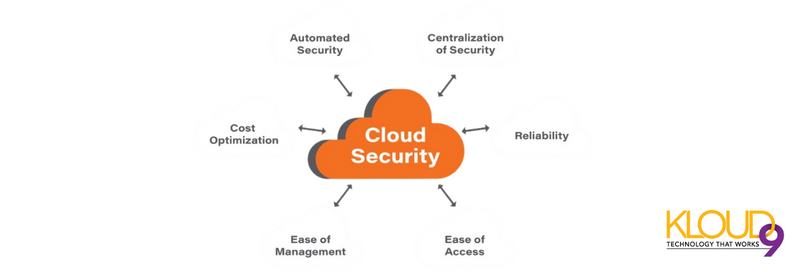
The Ultimate Guide To Protect Your Cloud Assets
Safeguarding social media: Tips for keeping your personal information protected
Here’s how SaaS can benefit your business
Should employers monitor remote employees?
The differences and benefits of two-factor and two-step authentication protocols

Both two-factor authentication and two-step authentication are processes that can help keep your business safe from data breaches. But while they serve the same purpose, these two methods are vastly different. In this blog post, we will discuss the differences between two-factor authentication and two-step authentication, as well as the benefits of each process.