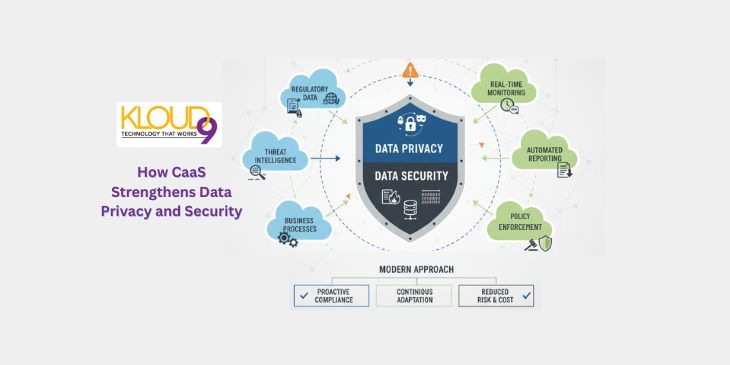
Compliance as a Service (CaaS) helps businesses manage data privacy and security without the complexity of DIY compliance. Learn how it works and why it matters.
CaaS for Data Privacy and Security: A Modern Approach
The Cost of Ignoring Spam Protection: Hidden Risk to Your Company

The digital era increases the risk of phishing attacks, spam emails, and malware threats. As an IT manager or a business owner, you must prioritize cybersecurity solutions to reduce the danger to your company data.
Since technological advancement presents opportunities and challenges, online safety and data protection are critical for IT consulting services.
What are identity and access management systems?

Businesses frequently deploy strong antivirus software and firewalls to protect themselves against cyberattacks, but relying on just those is not enough. A cutting-edge identity and access management (IAM) solution is essential for protecting your digital assets from hackers, rogue employees, and weak passwords.
Signs you have weak enterprise security

As cyberthreats become more sophisticated, many businesses need to prioritize cybersecurity more than ever. But are you sure that your security measures are keeping your enterprise IT assets safe? Here are five signs that they may not be effective.
Open wireless networks
With just one main internet line and a couple of wireless routers, an entire office can get online.
The business benefits of IAM

Your employees access applications and confidential business data every day. Hackers, on the other hand, are trying to do the exact same thing but for more malicious reasons. What’s worse, even employees can go rogue and steal your data, which is why it’s crucial that you have an identity and access management (IAM) solution in place.