- Columbus: (614) 702-7700
- Cleveland: (216) 393-2484
- Akron/Canton: (330) 685-9100
Vulnerability Management
Successful vulnerability management is being proactive instead of reactive
Hackers are constantly looking for ways to exploit vulnerabilities in your network. Vulnerability management is a way of addressing and remediating a company’s cyber vulnerabilities. Failure to properly assess and identify these vulnerabilities could lead to confidential and personal data to be stolen.
Using vulnerability management services from Kloud9 means that any potential, or current, holes in your security will be identified and fixed. We’ll help you implement security best practices and scan your cyber environment for vulnerabilities and risks. We will also help you implement security best practices and train your employees to stay safe online.
Kloud9’s vulnerability management is made of experts that work with you to develop a customized vulnerability management plan that meets your business’ specific needs
Here’s how we manage vulnerabilities in your network
Vulnerability Identification
Executive Reporting Tools
Risk Triage System
Patch Management

Want to learn more about how our Vulnerability Management services?
If you aren’t sure about how Vulnerability Management services affects your business, why not get an opinion from a security expert? Get in touch with us and we’ll set up a free consultation with our security expert, who will assess your cybersecurity solutions and answer any questions you might have about vulnerability management.
Featured Blogs

Tips for Improving Your Email Privacy and Security
Mitigate the effects of email-borne attacks by reading these tips.
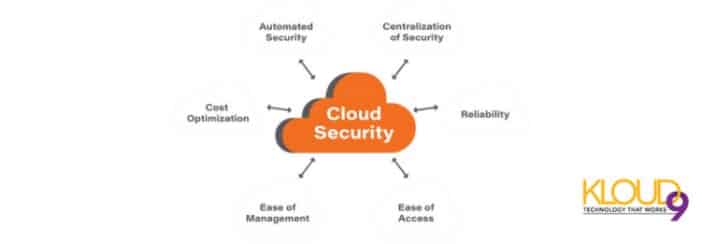
The Ultimate Guide to Protect Your Cloud Assets
Safeguard your cloud-based digital assets with effective vulnerability management and by staying in the know about common cloud threats.
8 Email Hacks You Never Knew Existed
Understanding these email hack techniques will help you anticipate the signs so you can avoid them altogether.
