There are more people and businesses who now take advantage of the cloud, and there are some who don’t even know they are using it. Unfortunately, when people are unaware that they are using the cloud, they are not as protected as they should be.
This is why it has become increasingly essential to understand how to protect or secure your information on the cloud. Below are some effective ways of safeguarding your data on the cloud.
1. Make use of a cloud service that encrypts
The first major step in the protection against identity thieves is making use of a secured cloud service that can encrypt your file both on your computer and in the cloud. Encryption makes sure that service providers and their service administrators, and also third parties are restricted from having access to your private information.
2. Read the user agreements
Never sign up for a cloud service without first reading and understanding the user agreement. User agreement includes essential information that explains how the cloud service secures your data and whether you grant them permission to make use of your information or in any way sell it when signing up.
It is risky for you to sign up for anything without first having a comprehensive understanding of the meaning of every clause in the agreement.
Anytime there is an update about your service provider’s privacy policies, you will be notified —either via text, an email, or by an alert when you log in. Always ensure you read these notifications to confirm that the changes do not affect your information negatively.
3. Set up your privacy settings
After you’ve signed up for a cloud service provider, you should immediately configure your privacy settings to make sure you’re not sharing your personal information through the apps connected to your service provider.
Also, you should determine how much and what type of information the service provider can pull from your app or devices. Check and re-configure your privacy settings at least every two weeks to be sure they are safe.
4. Use a strong password
A strong password is vital to every account you have, especially when it comes to securing accounts that have your private information. More than 75% of attacks are successful because of the use of weak passwords.
When creating your password, you must be diligent and creative about it. Never use a password that is shorter than eight characters. You should also avoid making use of identifying information such as your favorite pet name, your birthday, your name, your company name, or the names of your best friends.
You should never create a password that consists only of letters; make sure you use a mix of both uppercase letters and lowercase letters, and mix them up with symbols and numbers. Finally, regularly update your passwords and avoid making use of the same password for multiple accounts.
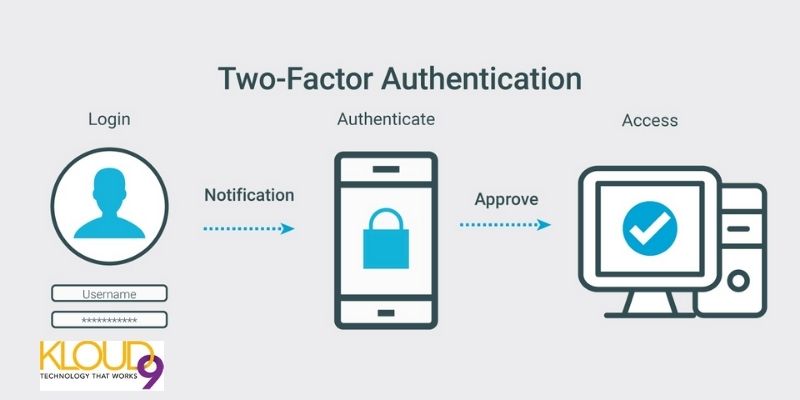
5. Use two-factor authentication
When offered this option, ensure you use two-factor authentication. With two-factor authentication, anyone who wants to sign into your account must provide additional information in addition to your password.
Common authentication methods include submitting a code that was sent to you via email or text by your cloud provider, providing a personal PIN, or answering a secret question. You can also download an authenticator app.
It’s not all accounts that will automatically request a secondary identifier, so ensure to check your settings to see if the option is available.
6. Don’t share personal information
Some of your information may look harmless, but if they fall into the wrong hands, it may leave your identity unprotected. Don’t ever make your mother’s maiden name or your birth date known publicly; they are asked often as questions for verification of your identity.
Also, avoid making people aware of information such as the name of your pet or the name of the street you grew up in. Irrespective of how well you know or trust someone, don’t ever give them the last four digits of your SSN (social security number).
Some cloud service providers will allow you to select questions you would like to answer for verification. If this option is available, make use of questions and answers that you can easily remember. Such question and answer shouldn’t be one that anyone close to you can correctly guess.
7. Don’t store sensitive information
Never store sensitive information such as your SSN, important financial statements, or copies of your identity cards on the cloud. You should also consider other essential information you wouldn’t want anyone to get their hands on.
Also, avoid keeping private pictures or personal interactions with partners on the cloud.
8. Use a strong anti-malware program
You need to have a very strong anti-malware and antivirus protection on your tablet, smartphone, laptop, and any other device that uses the cloud. A strong anti-malware program is needed because the cloud transmits information over the internet.
These apps or software help you to block suspicious downloads and URLs, and some even offer features such as device location services, backups, and remote wipes.
9. Install updates on your operating system
Most people often dismiss the notifications popping up on their smartphone or laptop, alerting them to update or upgrade their operating system. These updates are very important for the protection of your devices and information.
The updates are created to fix bugs that may be on your devices. By ignoring them because of their inconvenient timing, you are setting yourself up for even greater inconveniences. So, make sure you install all updates whenever they are available.
10. Be careful of how you use public Wi-Fi
Even if you use strong passwords, firewalls, anti-malware, and antivirus programs when using a home’s wireless connection, you can’t be so sure that a public connection is safe.
When you want to make use of public Wi-Fi, ensure you verify the connection through the business. Never use internet hot spots if the source is unverified. Hackers make use of these public Wi-Fi connections to steal data when you are connected to the spot.
Hackers or cyber thieves don’t need to be technologically advanced to steal your information. All they need is a small device and to be within 100 feet from you as you use the connection. For further protection of your information, always turn off your Wi-Fi feature until you need it.
Always make use of a VPN (a virtual private network) whenever you are viewing sensitive information in public.
Conclusion
The tips above are steps you can take to ensure that your data is safe on the cloud. However, hackers may still find their way into your private information even if you apply all the tips. So, if at any time you suspect your account has been compromised, immediately change your verification information and passwords, and also alert your cloud service provider.
When you report suspicious behavior to your cloud provider, it will help them in preventing future attacks.




You must be logged in to post a comment.