Many cybercrime attacks are carried out through emails. This is because email accounts are more vulnerable to these attacks. Phishing has been used time and time again to infiltrate companies; yet, email security is still not considered integral by many organizations.
Phishing is the act whereby cybercriminals target people through emails, text messages, or telephone and pretended to be a trusted contact. Phishing is an attempt to trick people into providing confidential information like passwords, contact information, bank credentials, social insurance numbers, or social security numbers. Once they gain access to this information, they can commit crimes such as financial fraud.
Most email accounts are connected to a lot of systems nowadays. These systems, which include industries like healthcare, retail, and governments, may be more susceptible to cyber-attacks. Through phishing crimes, criminals are now attacking the email accounts of companies. It is therefore important that employers, employees, and individuals improve their email security. Here are some best practices that will help improve your security against phishing:
1. Pick strong passwords
The most basic security requirement for your email is a strong password. Having a strong password will make it difficult for cybercriminals to gain control of your email account. Clearly stipulating a requirement to use a password manager is another good practice. This can be included as a part of the security policy of your company email accounts.
Your emails and company data contained in the official email accounts are more vulnerable to cyber-attacks if the passwords are weak.
2. Encrypt the contents of your email
To fully protect the contents of your email, it is required that both the attachments and contents are encrypted. It should be encrypted while it is in your inbox and when you are forwarding it to another account.
Some email platforms may not have the ability to encrypt your email contents fully against all cyber threats. However, there is a third-party add-in that provides these encryption services. They can help in closing any email security loop found. But some of these encryption services may affect the user’s experience. Ensure that you test all available options when choosing any of these services. An effective encryption tool should form a part of your usual workflow.
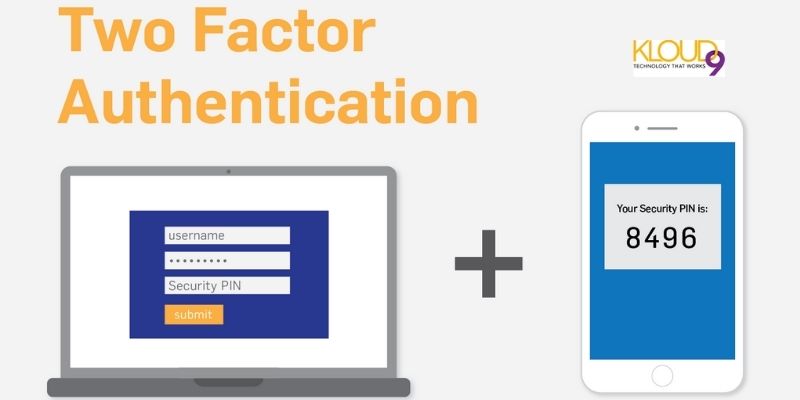
3. Use two-factor authentication
Using two-factor authentication may seem difficult, but it is one of the essential email security practices. It is a tool you can easily use to improve your email security. This authentication, be it a two-factor or multifactor authentication, helps you in creating a higher level of security that is more than having a strong password as the sole security measure. The two-factor is typically connected to an app or your mobile phone. A code will be sent to you via app notification or text message after you have signed in with your password. You will be required to enter this code before you can proceed to do anything on your email.
Cybercriminals who attempt to gain access to your email account through passwords will need to enter this code too. They will not be able to gain control of your email account if they do not have the authentication app or your mobile phone. Ensure that the two-factor message is never sent to your computer/laptop; this is important because the code could be easily visible to the cybercriminal if your device gets misplaced or stolen.
4. Never open unexpected attachments
Normally, you get emails with attached files. It is an everyday practice in the office. Opening these emails is always instinctive, but you have to be cautious about it. Take some time to review the email before opening it.
If you get an unexpected mail, try to verify the address of the email; display names should not always be trusted as they may be a spoof. It is safe to open emails from a client, coworker, or manager that regularly sends attachments to you.
There are email applications that can help scan viruses on incoming emails. These applications usually segregate “spam” emails with suspicious contents. Take time to review this setting in your email application.
5. Scan incoming emails
It is a good practice to scan all incoming mails before forwarding them to employees. There is anti-phishing software that can be used to scan every email. This software is capable of detecting the smallest details in any phishing emails. They can flag potential problems and quarantine suspicious emails.
You should get software capable of replacing links with proxies. They should be tested properly before forwarding them to the inboxes of your team members.
6. The company’s email should not be used for personal reasons
You make your company’s email account more vulnerable to cyber-attacks if you use it for personal reasons. There should be a policy in your company stating the acceptable use of their email accounts. The infrastructure of the company’s entire security program depends on this policy. It should specifically state the appropriate way to use the company email.
You will be exposing your company to cybercriminals if you use email accounts for activities like emailing friends, signing up for subscription services, or online shopping. Corporate email use should be restricted, and the company’s email account should not be used for personal reasons.
7. Avoid public Wi-Fi
Your email account is vulnerable to data hack if you make use of public access Wi-Fi. Cyber attackers find it easy to gain access if you connect to Wi-Fi that they have already programmed. It is, therefore, necessary that you use a Virtual Private Network (VPN) if you must use a public access Wi-Fi.
Not only will VPNs provide you more safety and security when you work in public, but they also encrypt your data. VPN will encrypt your data from end-to-end, securing and keeping private your company data. VPN services are easy to set up and implement, depending on the need of your organization. Choose a trustworthy VPN service when using public access Wi-Fi.
Conclusion
Nowadays, emails are channels of business communication mostly used by an enterprise. It is therefore important that this channel is safe and secure. It is easy to stave off data breaches and cyber-attacks if you implement essential email security practices for preventing phishing.




You must be logged in to post a comment.